There are many inaccurate portrayals of the Dark Web online and in popular media. I’m here to clear up these misconceptions and explain it plainly.
So what is the dark web? How does one get to it? What was it built for and why do people use it?
Note that this guide isn’t meant to teach you how to access and use the dark web. It’s just an explanation of what the Dark Web is. I won’t be sharing onion links to dark web marketplaces or other resources on this page, and I’d ask that you refrain from posting any related links in the comments. In no way do I condone using the Dark Web for nefarious purposes or other illegal activity.
Define: Dark Web
The Dark Web isn’t some mysterious place exclusively reserved for hackers, drug dealers, and criminals. It’s not its own network entirely separate from the rest of the web either. Anyone can visit the “Dark Web” and it’s actually quite simple. You can even access it from your cell phone.
To define it simply, the Dark Web is a part of the internet accessed through an anonymized network of computers known as darknets. It’s accessed through a browser known as Tor. From the user perspective, Tor functions nearly identically to any other browser. You simply install it and visit websites by typing in their addresses.
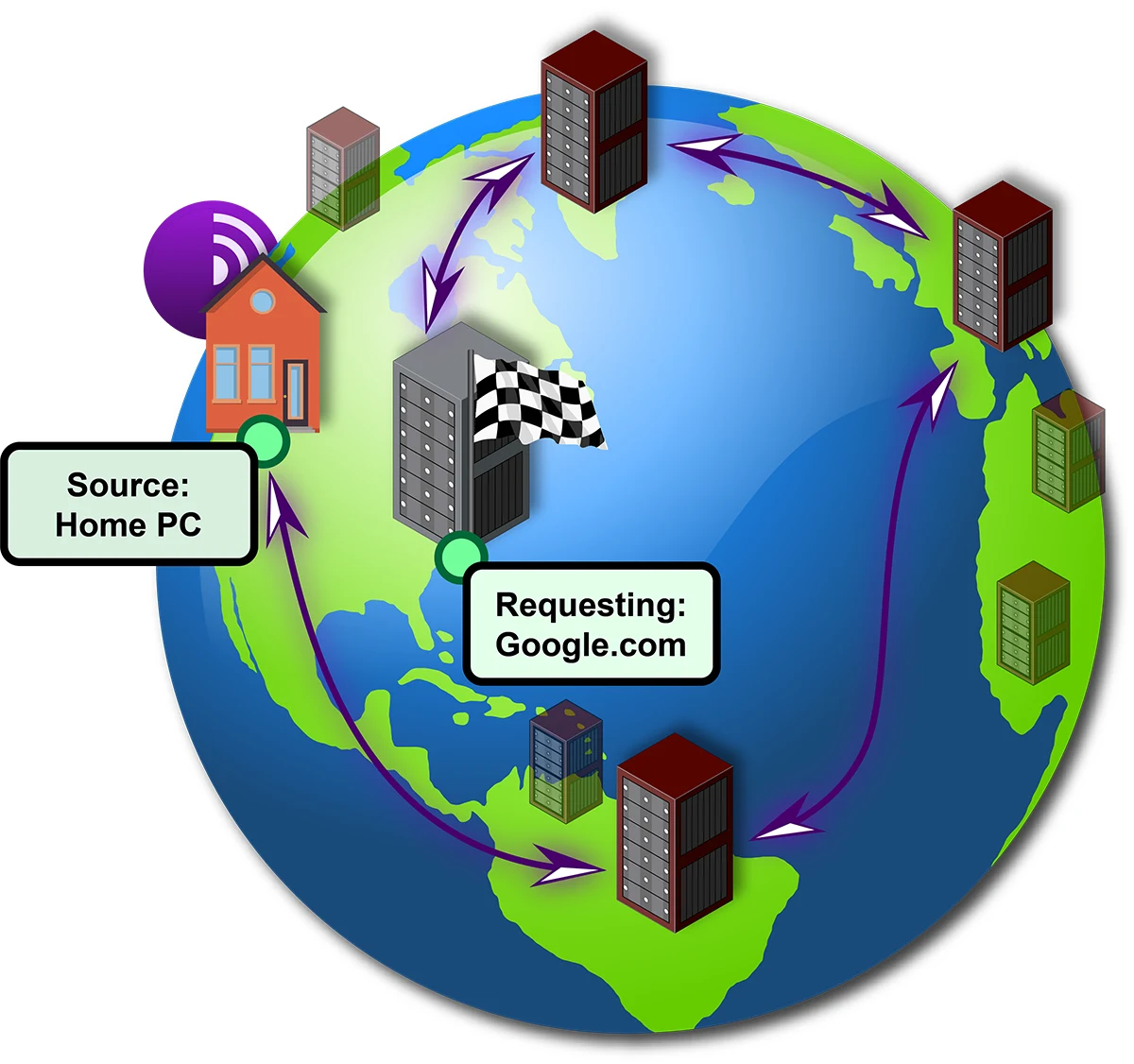
How it Works
Behind the scenes, Tor routes your data through a random encrypted network of computers before reaching the final destination. It is like a VPN, but with extra steps.
Tor is free to use. The network of computers that makes Tor possible and route its traffic does so voluntarily.
Unlike the regular internet, which tries to facilitate the most efficient communication between your computer and the website you’re visiting, Tor routes your traffic through three different volunteers which may be located any place on Earth. This means you can visit “Google.com” one minute and get the version in French, refresh the page and get it in Spanish or Japanese.
Since Tor routes your traffic all over the world, it takes significantly longer to load most pages. Unless you’re legally not permitted to access certain content (world news, YouTube, adult websites, etc.) because of political censorship, tyrannical government interference (e.g. China), or fear of being monitored, you’re likely better off just using a regular web browser to access the “regular” internet.
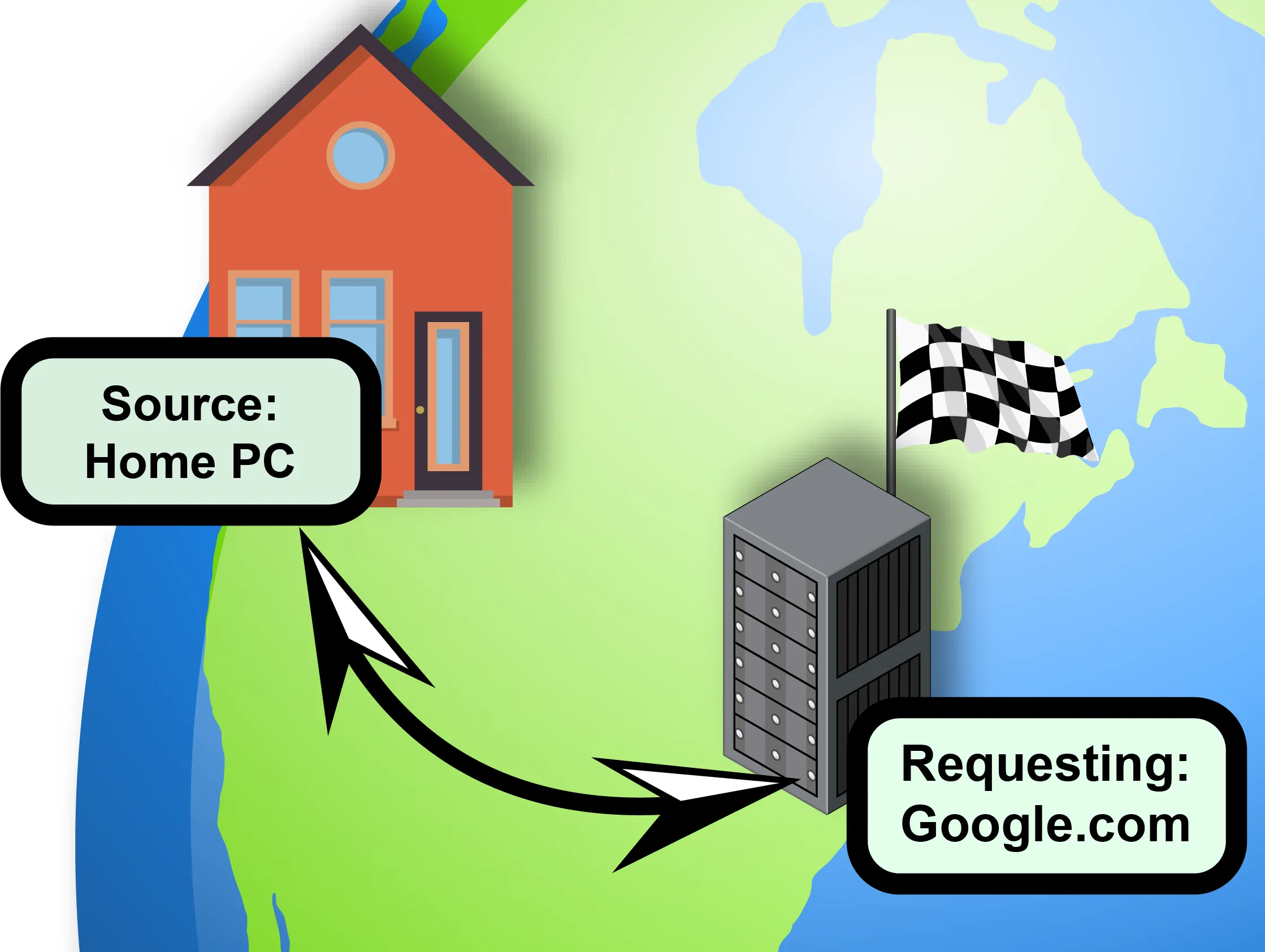
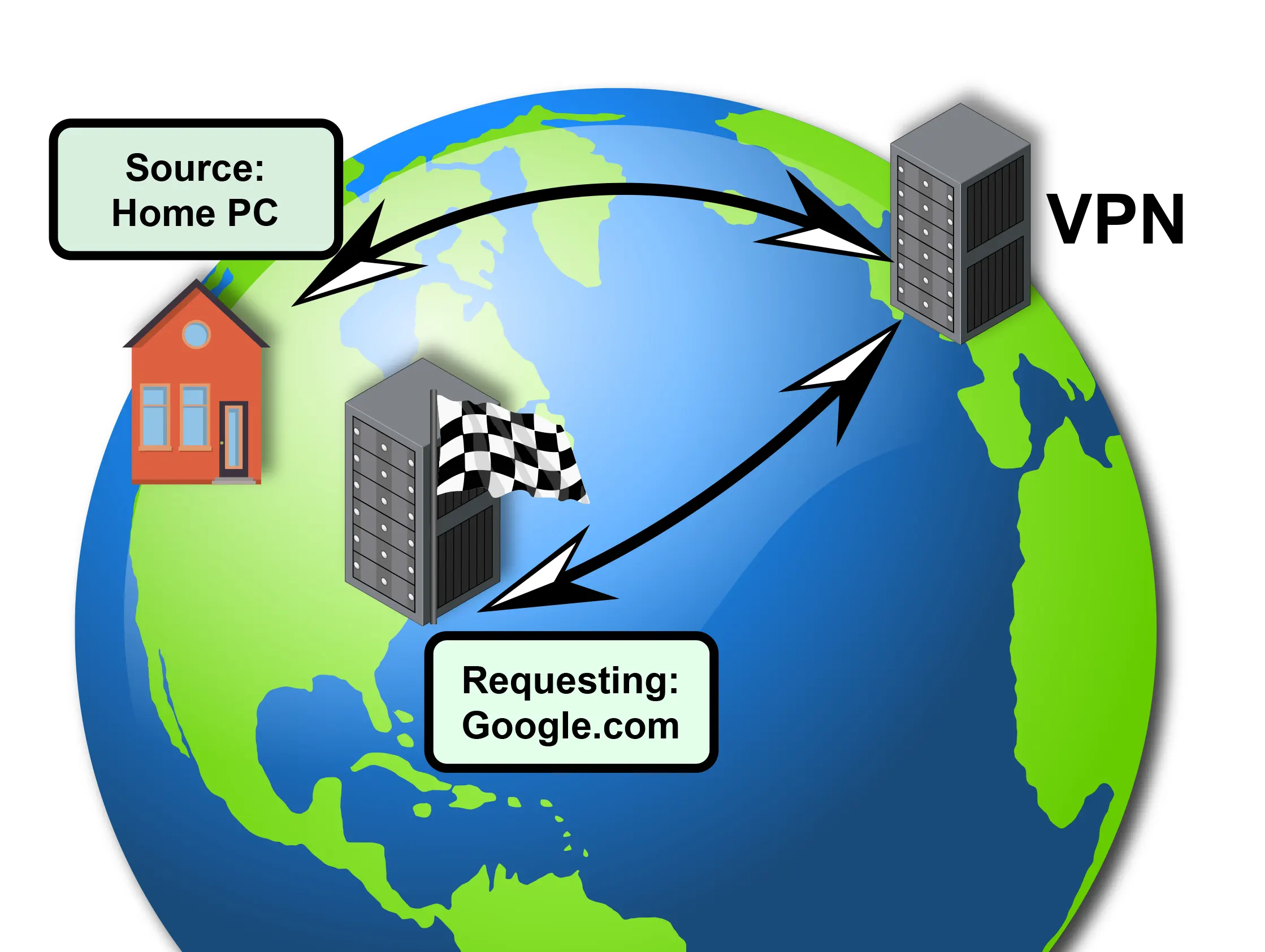
For comparison, here are diagrams illustrating what routes through a VPN and typical connection might look like.
Accessing The Dark Web (Tor)
The Dark Web can be accessed by installing the free Tor Browser. The Onion Routing Project (Tor)’s browser is based on the Firefox web browser and can be thought of as a modified, extended version of it that connects to the Tor network. So if you know how to use a web browser, you already know how to use Tor browser.
You can browse the web just as you usually would using Tor browser. However, the experience will be substantially slower than usual, since your traffic must be routed through random sources across the world.
Onion Links
A key feature of Tor is the ability to access dark web sites using Onion links. Rather than ending with usual domain names like .com or .net, onion links end with .onion, and can only be accessed using the Tor browser.
Domain extensions ending with .onion behave a little differently than traditional URLs or addresses. While by default, Tor encrypts your network traffic from your computer to the source and hides your identity, it does not hide the identity of the server you’re connecting to. When you access a site via .onion, both your computer and the server or site you’re connecting to are hidden and (mostly) anonymous. Rather than accessing a public service, like Google.com, you’re accessing a hidden service when you use .onion links.
Onion links hide the address of the server you’re connecting to. This adds a layer of protection for the website. The illegal sites and drug marketplaces online will end with the .onion extension, since traditional websites would simply be blocked and targeted by law enforcement.
If you access a website using a .onion extension, it will probably take even longer to load than a normal website accessed through the Tor network. These sites are often hosted in remote parts of the world with more lax legal laws and lack the funding or availability of more traditional (legitimate) websites. They’re often targeted with DDOS attacks and held for ransom, and may go down or disappear randomly without notice.
Use Case
Original Use Case
Tor was originally developed by computer scientists at the US Naval Research Laboratory in the 1990s with the goal of protecting sensitive information transmitted online. It was released to the public for free in 2004. By 2006, a nonprofit known as The Tor Project was established to continue maintaining the project. Branches of the US military continue using the Tor network to this day.
Bypassing Firewall/Restrictions
Did you know China filters and blocks out a significant portion of all traffic on the internet? It’s sometimes referred to as the Great Firewall of China. Vietnam, North Korea, Iran, Saudi Arabia, Ethiopia, and Syria are also examples of governments with oppressive internet restrictions.
Users in these countries may use Tor or VPNs to get around the restrictions imposed by their governments to access world news and other information.
Illegal Marketplaces
You may have heard of a dark web marketplace known as the Silk Road. It’s credited as the first large-scale modern dark-web marketplace. It was established in 2011 and you could think of it like eBay, but for drugs and fake driver’s licenses.
The service operated by allowing users to make anonymous(ish) purchases using the cryptocurrency Bitcoin. The sellers would then send the products to the user via the US Mail, and the user would leave feedback or reviews on the product after receiving it. This would build up the seller’s ratings and establish trust in the marketplace.
The US Government tried to crack down on the marketplace several times. But it would just reappear soon after, hosted on a different server.
Eventually, the owner of Silk Road, a US National named Ross Ulbricht, was arrested in 2013, over two years after the marketplace first went online after an investigation conducted by IRS agents. They make a connection between him and a message he posted online to market the website back in 2011.
Ross remains in federal prison and is serving two consecutive life sentences.
Many other dark web marketplaces have come and gone since the end of Silk Road, including Empire and White House Market. Besides the owners of dark web marketplaces being held accountable, drug dealers and users in these marketplaces have also been taken to court. Buying and selling drugs over the dark net is not a good idea. It relies heavily on the US Postal service to facilitate transactions, and anything done involving them constitutes a federal crime. You also never know what you’re getting, despite the review systems. A common example involves dealers selling pressed methamphetamine pills disguised to look like Adderall, opiates being laced with undisclosed amounts of fentanyl, and so forth.
The lure of easy money and quick access to drugs will surely drive people to continue creating and seeking dark web marketplaces. However, their days may be numbered as government agencies grow increasingly sophisticated in tracking activity occurring through Tor.
If you’re interested in learning more about dark net marketplaces, please check out my guide on the subject.
Other Nefarious Purposes
Besides the online drug trade, the dark web has facilitated many other illegal activities. I will not get into detail on each of these topics, but examples include:
- Buying, selling, trading, and sharing of illegal forms of pornography, child exploitation, human trafficking
- Sale of unregistered weapons or guns
- Hacking communities, marketplaces and forums for stolen personal information and credit cards, or identity theft
- Murder for hire services. The exact details appear inconclusive, we do not know if anyone’s really been able to hire an assassin online. There was a bounty list-type website promising crypto for kills, featuring prominent world leaders and celebrities. None of the people on the list were killed as a result of this.